IT Networking and Security
A strong business is built on a reliable, secure network. We provide a complete suite of IT networking and security services that provide an essential framework to prevent failure, ensuring seamless connectivity, robust protection, and peak performance for your entire IT infrastructure.
Networking & Switching
Network Switching & Routing: The Backbone of Your Business
At the core of every high-performing business is a reliable and intelligently designed network. Our Network Switching & Routing services provide the critical foundation for your entire IT infrastructure. In today's fast-paced digital world, your business relies on seamless, secure, and uninterrupted data flow—from sending an email to hosting a video conference with a client on the other side of the globe. We ensure your network is not just functional, but an asset that drives productivity and collaboration.
We specialize in designing and deploying robust network architectures that eliminate bottlenecks and optimize data transmission. Network switching allows for lightning-fast communication between devices within a local network, ensuring your team can access shared files and resources instantly. We select and configure enterprise-grade switches that offer high port density, Power over Ethernet (PoE) capabilities, and advanced security features, tailoring the solution to your specific operational needs. Our goal is to create a network that supports your current demands and is scalable for future growth without compromising on speed or security.
Beyond your local network, network routing is what connects you to the outside world. Routers act as the intelligent traffic cops of your network, directing data to its correct destination, whether it's on the internet or a remote branch office. We configure and manage high-performance routers to ensure secure and efficient data transfer, prioritizing critical applications like VoIP calls and video streams to guarantee a flawless user experience. Our expertise in routing protocols and WAN optimization ensures that your long-distance connections are just as fast and reliable as your local ones.
Our service doesn't end with installation. We provide comprehensive support and maintenance to ensure your network remains healthy and secure. Our team proactively monitors your switching and routing infrastructure, identifying and resolving potential issues before they can impact your business. We believe a strong network is a silent partner in your success—it works flawlessly in the background, allowing you to focus on what you do best. With our Network Switching & Routing services, you gain a powerful, dependable, and future-proof network that you can count on, every day.






Wireless
The Freedom of Secure Wireless Connectivity
Break free from cables without sacrificing security or performance. We design and deploy high-speed, secure wireless networks that provide seamless connectivity and uninterrupted access for your team. Our solutions are built for agility, allowing your business to stay productive from any location.
In the modern workplace, a fast and reliable wireless network is no longer a luxury—it’s a necessity. It’s about more than just convenience; it’s about giving your team the freedom to collaborate and innovate from anywhere in your office, without being tied to a desk. Our wireless solutions are designed to provide the seamless connectivity you need, while ensuring the highest levels of security.
We specialize in designing and deploying scalable Wi-Fi networks that support high device density and demanding applications. We conduct thorough site surveys to identify optimal access point placement, ensuring strong signal strength and consistent performance across your entire workspace. Our solutions go beyond simple access by incorporating enterprise-grade security protocols, including guest access controls and robust encryption, to protect your network from unauthorized entry and cyber threats.
Whether you're a small office or a large enterprise, our team ensures your wireless network is both agile and reliable. Our systems are built to support the latest technologies, providing the bandwidth and stability your team needs for uninterrupted video conferences, cloud-based applications, and real-time collaboration. With our professional wireless deployment, you can empower your business with a secure, high-speed network that keeps pace with your ambition and growth.
We design and deploy robust Wireless Solutions for seamless, high-performance office connectivity. This includes secure, enterprise-grade Wi-Fi with VLAN segmentation to isolate guest, voice, and staff traffic. We implement WPA3 encryption and centralized Network Access Control (NAC) to ensure only compliant devices connect, delivering both speed and comprehensive wireless security.




Firewalls & UTM
Firewall & UTM: Your All-in-One Security Shield at the Network Edge
Protecting your business is our top priority. Our Firewall and Unified Threat Management (UTM) services act as your first line of defense against online threats. We'll set up and manage a comprehensive security system that protects your data from viruses, malware, and unauthorized access, giving you complete peace of mind.
In today's interconnected digital landscape, cyber threats are not a matter of if, but when. Your network's security is paramount, and a robust defense begins with your Firewall and Unified Threat Management (UTM) systems.
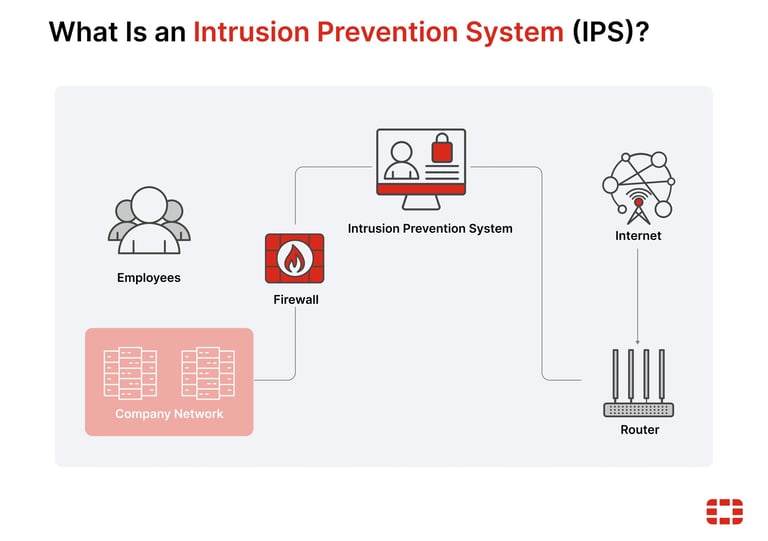
A firewall serves as the essential first line of defense, acting as a digital gatekeeper that meticulously inspects and controls all incoming and outgoing network traffic. It operates based on a set of pre-defined security rules to block unauthorized access and malicious activity, creating a secure perimeter around your valuable data and systems.
Our UTM solutions take this foundational security to the next level. Instead of managing multiple standalone security products, UTM unifies a comprehensive suite of security functions into a single, cohesive system. This includes advanced features such as:
Intrusion Prevention Systems (IPS): Proactively identifies and blocks sophisticated attacks in real-time.
Gateway Antivirus: Scans all incoming traffic for viruses and malware before they can reach your network.
Web Filtering: Protects your team from visiting dangerous websites that host phishing or malicious content.
Spam Filtering: Keeps your inboxes clear of harmful and unwanted emails.
By deploying a custom-configured UTM solution, we not only provide a powerful shield against a wide range of cyber threats but also simplify your security management and reduce overall costs. This integrated approach ensures your business operates securely and with complete peace of mind, allowing you to focus on growth and innovation.


SD-WAN
SD-WAN: Secure, Agile Connectivity to Optimize Every Path to the Cloud and beyond
Simplify how your offices connect. SD-WAN modernizes your network across multiple locations, providing seamless, high-performance connectivity that is both easy to manage and cost-effective. We help you centralize control and optimize your network to ensure your multi-branch operations run smoothly.
For businesses with multiple branches or a distributed workforce, managing a traditional Wide Area Network (WAN) can be complex, costly, and inefficient. Traffic bottlenecks, high-priced dedicated circuits, and lack of visibility often hinder productivity and slow down critical applications.
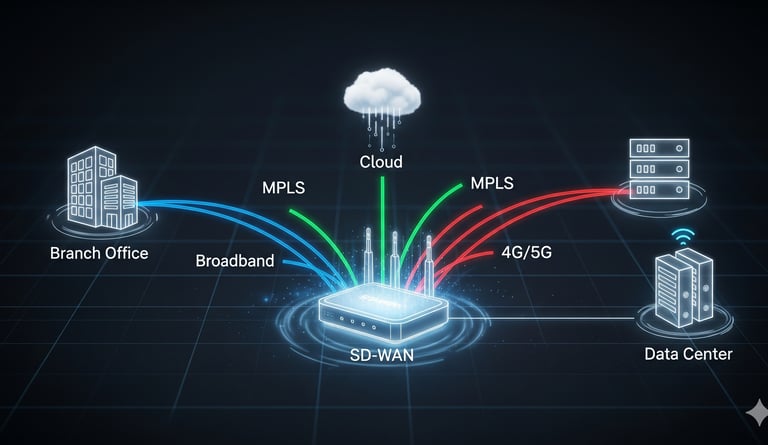
SD-WAN (Software-Defined Wide Area Network) is the modern solution to these challenges. It fundamentally transforms your network by using software to intelligently manage and optimize connectivity across all your locations. Instead of rigid hardware-based routing, SD-WAN dynamically directs traffic over a mix of connections—including cost-effective broadband, cellular, and traditional MPLS circuits—to ensure your business-critical applications always have the best path.
Our SD-WAN solutions deliver a range of powerful benefits:
Optimized Performance: Experience seamless performance for your cloud-based applications, video conferencing, and VoIP calls. SD-WAN intelligently prioritizes traffic to prevent lag and ensure a flawless user experience.
Cost-Effective Scalability: Reduce your reliance on expensive dedicated lines by leveraging a mix of affordable network connections. This allows you to easily and cost-effectively add new branches or remote workers as your business grows.
Centralized Control: Gain full visibility and control over your entire network from a single, easy-to-use dashboard, simplifying management and troubleshooting.
Enhanced Reliability & Security: With built-in redundancy and advanced security features, SD-WAN ensures your network remains secure and operational even if a connection fails.
By adopting an SD-WAN solution, you can unlock a faster, more flexible, and more resilient network that is perfectly aligned with the needs of your modern enterprise.



Structured Cabling - Passive






Your Future-Proof Foundation for Flawless Network Performance
Structured cabling is the organized, standardized physical cabling system that forms the foundation of a modern IT network. It's designed to support multiple hardware uses—like data, voice, and video—all through a single, unified, and easy-to-manage infrastructure.
Structured cabling moves away from "point-to-point" or messy, ad-hoc wiring. Instead, it follows a meticulous, hierarchical topology governed by international standards (like ANSI/TIA-568).
This standardization ensures:
Predictable Performance: Guarantees signal integrity and reliable data rates.
Scalability & Flexibility: Makes it easy to accommodate moves, additions, and changes (MACs) without disrupting the entire network.
Simplified Troubleshooting: An organized system reduces downtime and makes maintenance and repairs easier.
A structured cabling system is typically divided into six distinct subsystems, each serving a specific function:
By adhering to these subsystems and industry standards, a business builds a future-proof foundation capable of supporting current and emerging technologies, from high-speed data networks to Power over Ethernet (PoE) applications.
Cable Testing
The performance of your network hinges on the quality of its physical cabling. Our professional cable testing and certification services provide a vital assurance of your network’s health. Using industry-leading tools, we meticulously test every connection to verify it meets performance standards, identify hidden faults, and prevent future issues. This process ensures your network can support high-speed data, Power over Ethernet (PoE), and the bandwidth demands of modern applications, guaranteeing peak performance from day one.
Fiber Optic Networking
In a world where data-intensive applications are the norm, traditional copper cabling often falls short. Our fiber optic networking solutions offer the ultimate upgrade, transmitting data as pulses of light through thin strands of glass. This technology provides unrivaled speed and bandwidth over long distances, making it immune to electromagnetic interference and ideal for mission-critical applications. We design and install a robust fiber optic backbone that is not only a game-changer for today's needs but also a future-proof investment for your business.
IT Networking & Security FAQs
Why is my Wi-Fi so slow?
Common causes for slow Wi-Fi include network congestion (too many devices), poor router placement, signal interference from other devices, or an outdated router.
How do I troubleshoot a network issue?
You should start with a simple power cycle of your modem and router. If that doesn't work, check your physical connections (cables and ports). You can then use command-line tools like ping to test connectivity to other devices on the network.
What's the difference between a LAN, WAN, and VLAN?
A LAN (Local Area Network) connects devices over a small, confined area like an office or home. A WAN (Wide Area Network) connects networks over a large geographic area, like the internet. A VLAN (Virtual Local Area Network) is a logical grouping of devices that lets you segment a single physical network into smaller, isolated networks.
What is the difference between a switch and a router?
A switch connects devices within a single network (like computers and printers in an office), while a router connects multiple networks and directs traffic between them (for example, connecting your home network to the internet).
Why is managed IT services important?
Managed IT services are crucial because they transform a business's approach to technology from reactive (fixing problems after they happen) to proactive (preventing problems before they occur). By outsourcing the management of your IT infrastructure to a Managed Service Provider (MSP), you gain a host of benefits that are critical for modern business growth, security, and efficiency.
My computer in the office is running very slowly when accessing files from the central server, but others in my department are fine. What's the first thing my IT team will likely check?
They'll check the speed settings of your computer's network plug. It might be set to run slowly (like an old highway) while the network is running fast (like a new expressway). Fixing this mismatch usually restores your speed.
Our company just installed 20 new internet-based phones, and now all video calls are choppy and delayed. What important setting needs to be fixed on the network?
The network needs to be told to prioritize the phones. This is called Quality of Service (QoS). It tells the network to deliver voice and video traffic first, making sure calls sound smooth even when everyone is downloading files.
How to set up a secure office network?
Setting up a secure office network requires physical security (locking equipment), network segmentation using VLANs to isolate traffic, and a robust Next-Generation Firewall (NGFW) for edge protection. Crucially, implement Multi-Factor Authentication (MFA) for all remote access and keep all networking hardware patched and monitored 24/7 to prevent both external attacks and internal unauthorized access.
What is a firewall?
A firewall is a security system that monitors and controls incoming and outgoing network traffic. Think of it as a barrier between your internal network and the outside internet, protecting you from threats.
What's the main difference between a firewall and a UTM?
A firewall is a basic security tool that filters network traffic based on a set of rules. A UTM (Unified Threat Management) is a more comprehensive security solution that combines the functions of a traditional firewall with other features like antivirus, anti-spam, intrusion detection, and content filtering into a single device. A UTM offers all-in-one protection, while a firewall is just one part of your security strategy.
How often should I update my firewall or UTM?
You should update your firewall and UTM continuously. Updates provide patches for newly discovered vulnerabilities and include the latest threat intelligence to protect against emerging cyberattacks. Many UTMs automatically download and apply these updates, ensuring your network is always defended.
What is structured cabling?
Structured cabling is the standardized and organized approach to designing and installing a complete system of wiring, cables, and hardware for a building's network infrastructure. It's a "passive" system because it's the physical foundation on which active network devices (like switches and routers) operate.
What are the key components of a structured cabling system?
The main components include telecommunications rooms or closets, where equipment like patch panels and switches are housed; horizontal cabling, which runs from the telecommunications room to individual wall outlets; and backbone cabling, which links different telecommunications rooms together, often between floors or buildings.
Why is it better than traditional cabling?
Structured cabling is more reliable and easier to manage. Unlike traditional, point-to-point cabling that can be messy and hard to troubleshoot, a structured system is highly organized, labeled, and standardized. This makes it far more scalable, supports a wider range of applications, and simplifies any future upgrades.
What are the different types of structured cabling?
The most common types are Twisted-Pair Copper (like Cat5e, Cat6, and Cat6A) and Fiber Optic cables. Copper is widely used for most standard network connections, while fiber is preferred for high-speed, long-distance data transmission between buildings or floors.
How do you ensure the quality of a structured cabling installation?
Quality is ensured through adherence to industry standards and rigorous cable testing. After installation, every cable run is tested for performance metrics like signal integrity, length, and continuity to ensure it meets the required standards (e.g., TIA/EIA).
What is SD-WAN vs MPLS?
SD-WAN (Software-Defined Wide Area Network) and MPLS (Multiprotocol Label Switching) are two different networking approaches used to connect geographically separated office locations and data centers (a Wide Area Network, or WAN). While both aim to provide reliable, high-performance connectivity, they differ fundamentally in architecture, flexibility, cost, and how they handle traffic.
We use (MPLS) private lines for all office-to-office communication. We want faster connections but need guaranteed quality for our VoIP calls. How does SD-WAN help us here?
SD-WAN allows you to use cheaper, high-speed internet connections (like broadband or 5G) while maintaining the quality you need. It uses "application-aware routing" to constantly monitor all available links. If one link slows down, SD-WAN instantly steers critical traffic (like VoIP) over the faster, better-performing link, ensuring call quality is never compromised.
We have multiple devices (printer, phone, PC) that all need a network connection, but the wall only has one active network jack. Is there a secure way to connect them all?
The safe and proper way is to install a small, managed network switch at the desk. You plug the wall jack into the switch, and then plug all your devices into the switch. A managed switch is preferred because it can be configured to use separate VLANs for each device (Voice, Data, etc.) for security and organization.
What is the difference between a Firewall and Antivirus software, and do we need both?
A Firewall is like the security guard at the gate; it controls what traffic can enter and leave your network. Antivirus is the security within the building; it detects, prevents, and removes malicious software already on a computer. You absolutely need both for comprehensive security.
What is the most common way our network security gets bypassed, and what is the best defense?
The most common bypass is through Phishing or Social Engineering—tricking an employee into giving up credentials or clicking a malicious link. The best technical defense is Multi-Factor Authentication (MFA), which stops a hacker from logging in even if they have the correct password.
What are the different types of network security?Network security isn't a single product; it's a comprehensive set of policies, controls, and tools designed to protect the integrity, confidentiality, and accessibility of computer networks and data. These measures can be categorized by their approach: Physical, Technical, and Administrative.
What are the core principles of network security? Network security is based on three core principles, often called the CIA triad: Confidentiality, Integrity, and Availability. These principles ensure that sensitive data is kept private, accurate, and always accessible to those who are authorized to use it.
What is a "Zero Trust" model, and why are companies adopting it for network security?
The Zero Trust model is a security philosophy built on the idea that you should "never trust, always verify." It assumes that threats can exist both outside and inside the network perimeter. Instead of trusting users or devices just because they are connected, every access attempt is verified and limited to only the resources absolutely needed, greatly reducing the impact of a breach.
Follow us
Support
info@delta8.in
+91 22 69309205
© 2025. All rights reserved.
Terms & Conditions
Privacy Policy
